Supported Data Models
Required Parameters
These parameters are mandatory for the connector to authenticate and function properly.| Variable | Description |
|---|---|
Instance Name | Your ServiceNow instance name(if the instance url is https://devxxxxxx.service-now.com - put the instance name as devxxxxxx) |
Username | Your ServiceNow username |
Password | Your ServiceNow password |
Creating a ServiceNow User for Leen Integration
This guide walks you through creating a ServiceNow user and assigning the appropriate roles to enable Leen to connect and interact with your ServiceNow instance.Create a User
- Login to ServiceNow portal using admin privilges.
- Navigate to All > User Administration > Users
- Select New
- Fill in the mandatory fields on the form:
- User ID - This will be used as the username in the Leen connection
- Complete all other required fields and save the record
- Set up the user’s password:
- After saving, select Set Password
- Create a password that can be permanent or temporary
- Copy this password for use in the Leen connection configuration
- If you check
Password needs reset, the user will be required to change the password during first login - For API-only access where the user doesn’t need ServiceNow UI access, you can set appropriate restrictions
Assign Roles
- Navigate to All > User Administration > Users
- Open the previously created user record
- Scroll down to the Roles related list
- Click Edit
- Assign following roles by dragging them from the left bucket to the right:
Role Options
| Role | Description |
|---|---|
sn_compliance.reader | Provides read-only access to GRC data |
survey_reader | Provides read access to all assigned assessments and questions |
- Select Save to apply the role assignments
Pre-requisites and Configuration Requirements
To ensure seamless data interaction between Leen and ServiceNow GRC, you must perform specific configurations related to the integration user and ServiceNow table metadata. These configurations enable Leen to submit and update GRC assessment responses programmatically.User Configurations
The ServiceNow user configured for Leen must have sufficient privileges to submit assessments programmatically.-
Make sure the user has required roles
ServiceNow assessment templates can have role-based restrictions, which determine which users are permitted to submit assessments. Typically, the default role sn_compliance.reader is sufficient and already covered in the earlier section. However, if certain assessment templates use additional or custom roles, those roles must be explicitly assigned to the integration user. This ensures Leen can automatically submit assessment responses without permission errors.
Steps to verify and configure required roles:
- Navigate to asmt_metric_type.list in ServiceNow.
- Apply the filter: Table = sn_compliance_control
- Open the desired Assessment Template record.
- Review the Roles field to identify which roles are required for users submitting assessments using this template.
- If roles other than sn_compliance.reader are listed, ensure they are added to the integration user account configured for Leen.
-
Add the Configured User as a Respondent in the Policy and Compliance Control Form
ServiceNow automatically generates assessment instances only for Controls that have at least one Respondent assigned.
To enable Leen to submit responses programmatically, ensure the integration user is added as a Respondent in each Control for which automated assessment submissions are expected. Steps to add a respondent:- Navigate to Policy and Compliance → All Controls.\
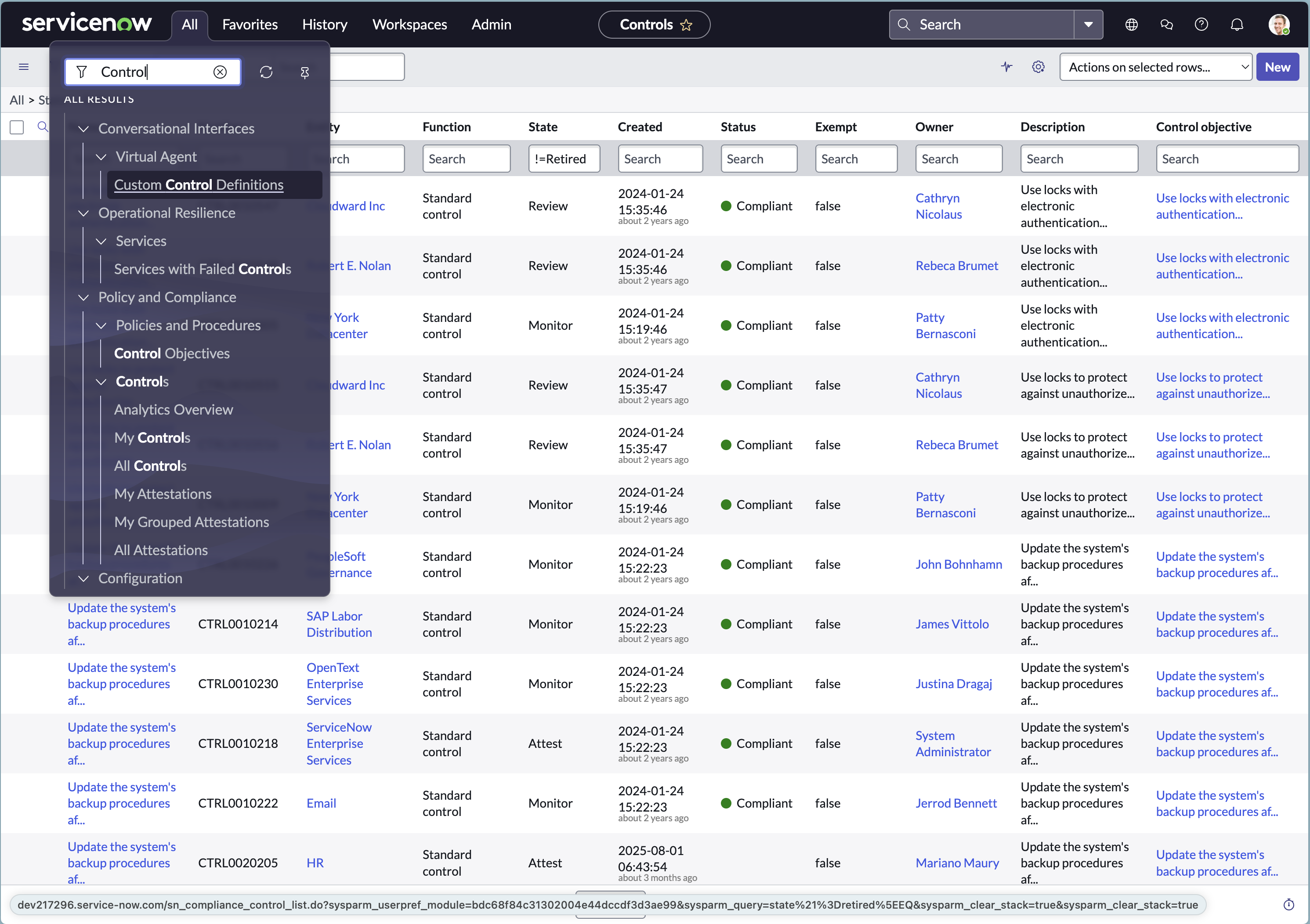
- Select the Control record for which you want to add a respondent.
Ensure the Control is in Draft state before making any changes. - Under the Assessment tab, there’s an option to add respondent. Search the configured user and add.
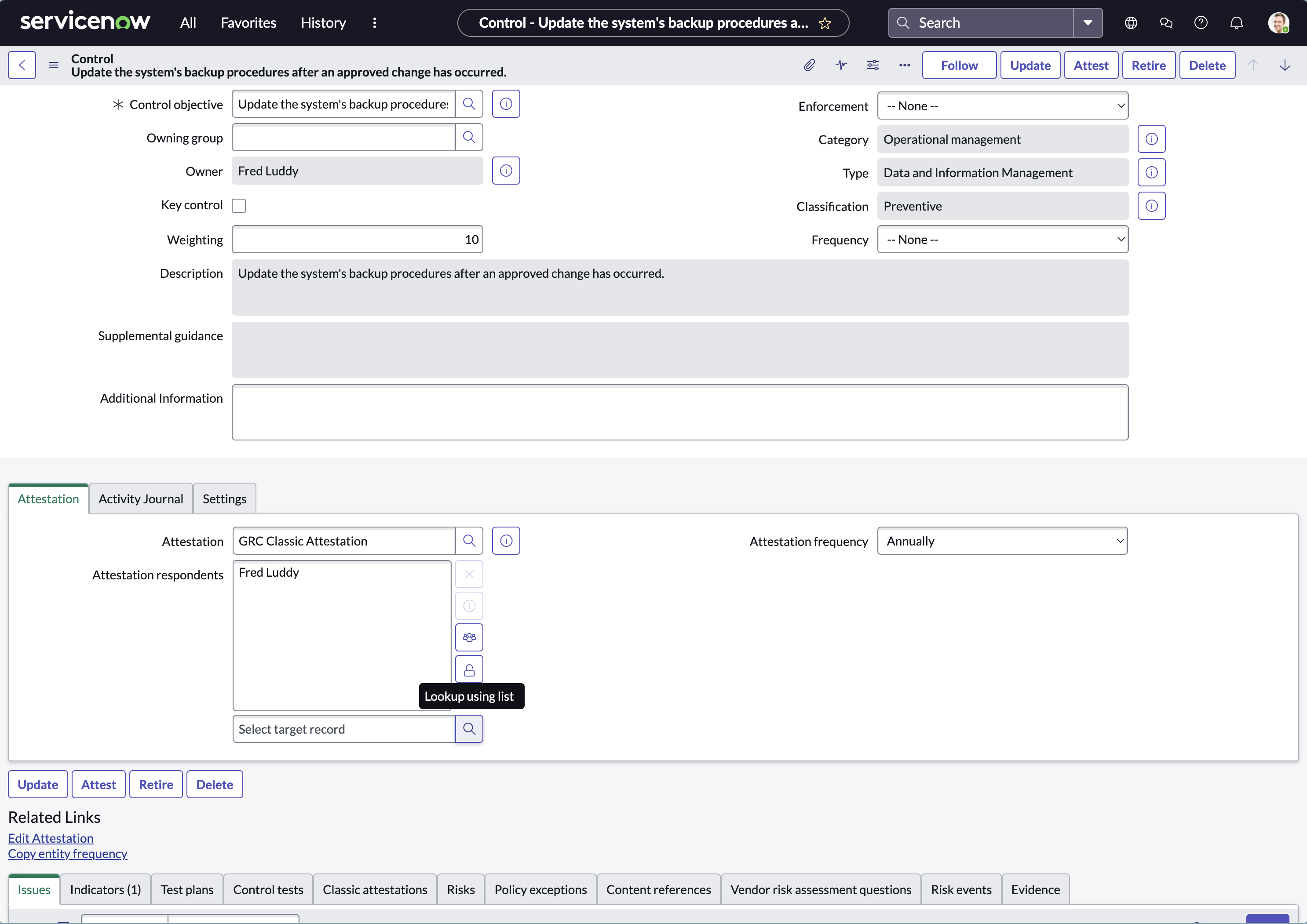
- Save the changes.
- Repeat the process for all relevant Controls.
- Navigate to Policy and Compliance → All Controls.\
-
Ensure assessments are assigned to the configured user
Only assessments assigned to the configured integration user can be successfully submitted.
ServiceNow’s out-of-box (OOB) rules prevent submission of assessments by superior roles, even if they have higher privileges.
Assign the assessments directly to the integration user to avoid submission errors.
Changes in Table Metadata
By default, certain assessment-related fields in ServiceNow are read-only, preventing API-based updates.To enable Leen to record assessment responses, you must uncheck the Read-only property for specific fields.
Tables and Fields to Update
| Table | Fields to Modify | Purpose |
|---|---|---|
asmt_assessment_instance_question | value | Required for recording numerical and text-based responses |
asmt_assessment_instance_question | string_value | Required for recording numerical and text-based responses |
asmt_assessment_instance | state | Required for updating the state of an assessment upon submission |
Steps to Make Fields Editable
- Navigate to sys_dictionary.list. Enter ‘sys_dictionary.list’ in the navigation bar and hit Enter.
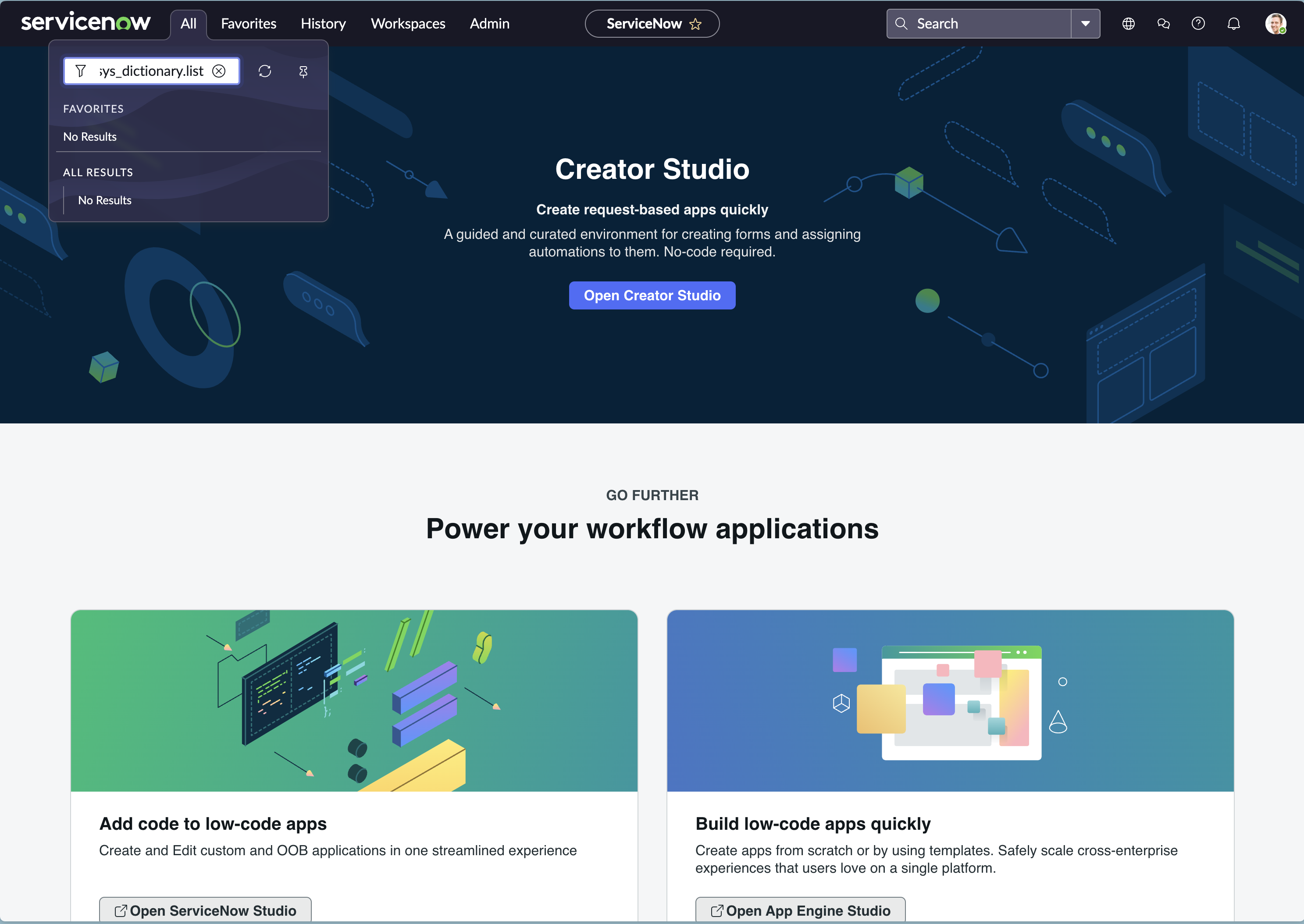
- Configure the filter as per the table mentioned above and filter the record.
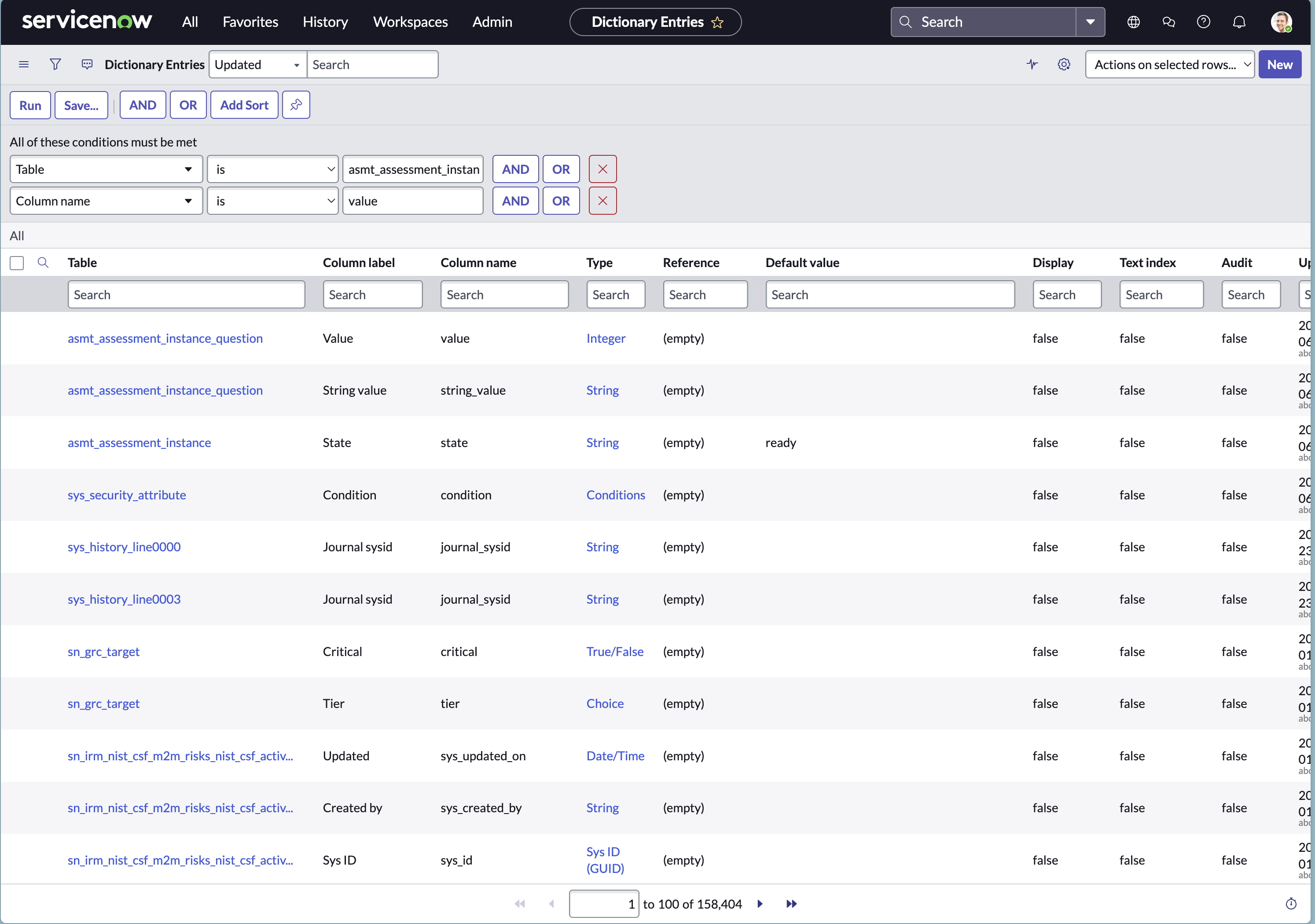
- Open the record and uncheck Read-only\
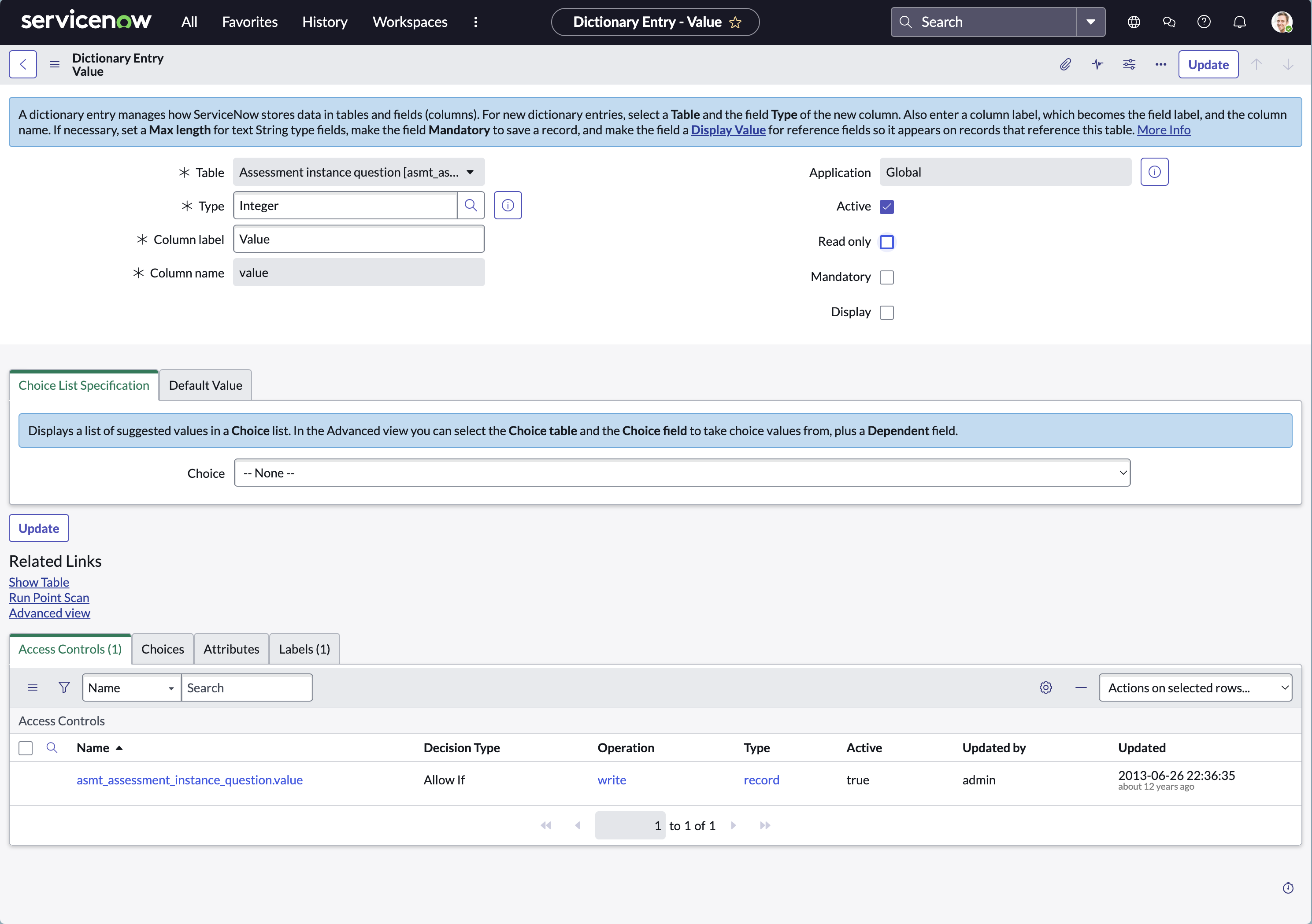
- Click Update to save the change
Why this step is necessary:
These fields are locked for manual editing by default. Leen updates them programmatically when submitting responses.
Temporarily unchecking Read-only allows the connector to write data into these fields.
Make string_value Field Editable
ServiceNow applies Access Control Lists (ACLs) at both the table and column levels to provide fine-grained control over which users can read or write specific fields. By default, the asmt_assessment_instance_question table includes an ACL for the value column (used for numeric or integer-type responses), but no ACL is defined for the string_value column, which is required to capture assessment responses that are of type string. Without this ACL, the integration user will not be able to submit or update string-based responses programmatically. To resolve this, we must manually create an ACL for the string_value column, using the existing ACL for the value column as a reference. Prerequisite: User should be elevated to security_admin role.Steps to create ACL for string_value:
- Navigate to System Security > Access Control(ACL).
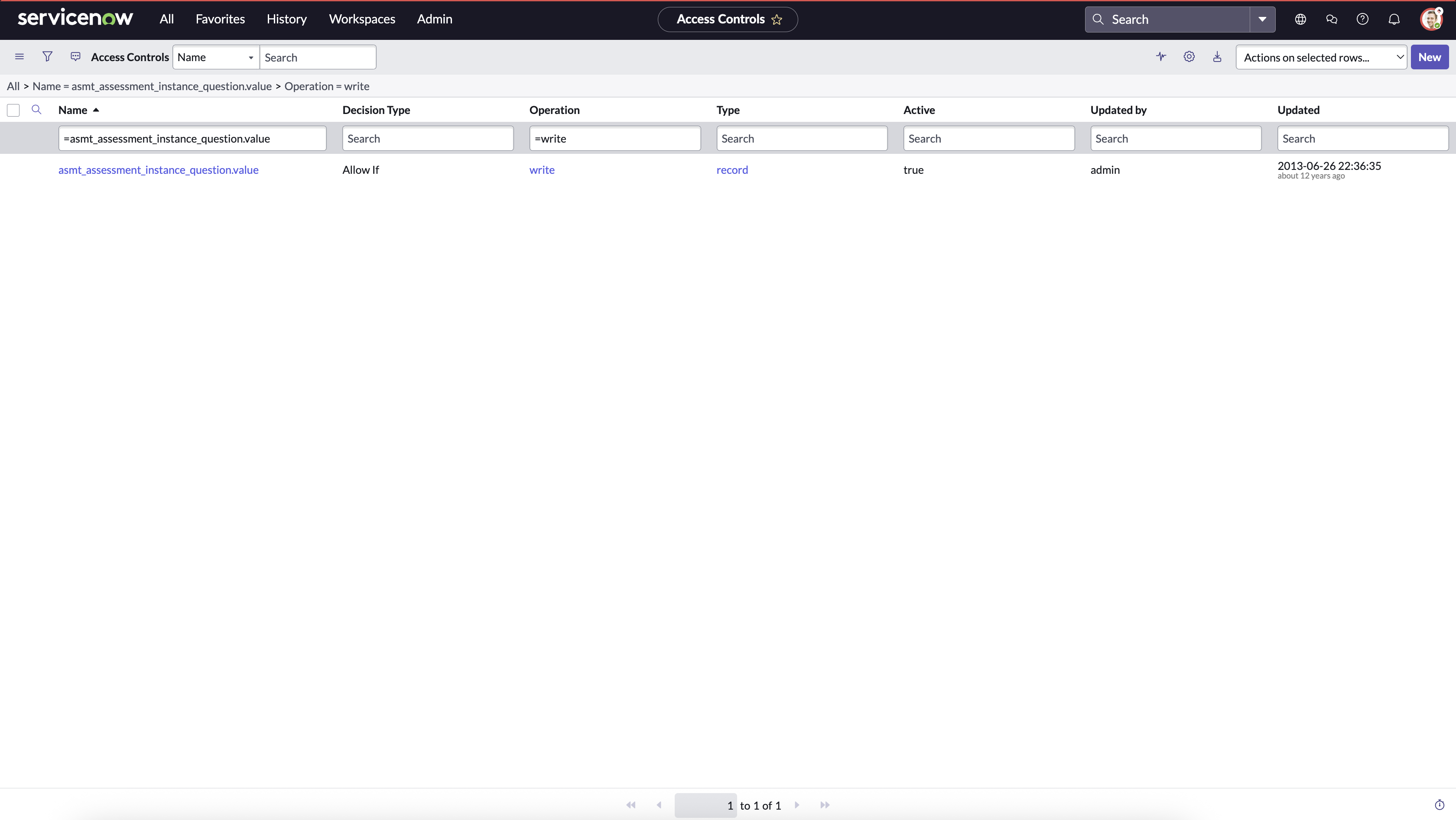
- Apply following filter:
- Name is asmt_assessment_instance_question.value.
- Operation is write.
- Open the record in new tab (This will be a reference record for us).
- Go back to the tab where the list was opened.
- Click New.
- Refer to the record opened in step 3 and create similar record like that record, except change the field from value to string_value.
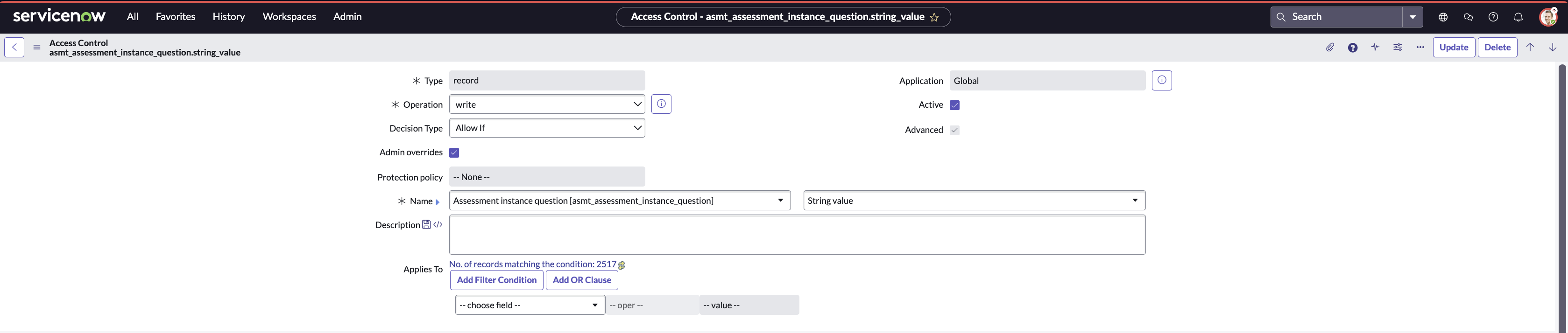
- Save the record.
Attachment Question Handling
When an assessment question is of type Attachment, the evidence file must be available as a publicly accessible URL.- Host the attachment in a location accessible via HTTPS (e.g., a presigned S3 URL).
- Leen will fetch this file and attach it to the assessment response automatically.
Note: Private attachments that require authentication cannot be processed by the integration.
Assessment Response Submission and Job Tracking
After Leen submits a response to assessment, the API endpoint returns a Job ID.This Job ID can be used to monitor the processing status of the submission.
- Response Payload: Includes a unique Job ID
- Usage: Use this Job ID to query submission status and confirm completion
- Refer Outbound Jobs