AWS Access Analyzer
AWS Access Analyzer helps you identify resources in your environment that are shared externally. This service analyzes your AWS environment for supported resource types and generates detailed findings about the access granted to those resources. Leen normalizes your AWS Access Analyzer data into a standardized model, providing deeper insights and visibility into how resources are shared across your AWS environment.Authentication Methods
Leen supports a couple of different ways to authenticate with AWS Access Analyzer. Here is a quick overview of the three different ways:- AWS Direct Access: This is the simplest way to authenticate with AWS Access Analyzer. It requires the AWS Access Key ID and AWS Secret Access Key.
- Leen Role Creation: Your end-user will have to create a new IAM role that Leen can assume. This role will only require the minimum permissions to read from Access Analyzer.
- Role Chaining: This method involves creating a new IAM role in your account which has permissions to assume roles in your end-user’s account. Leen will then setup a role and trust relationship to use this role with permissions to the end-user’s Access Analyzer.
Prerequisites
We need to create a new policy to allow generate finding recommendations from Access Analyzer. you can follow these steps to create a new policy:Create a new Policy
In the AWS console, navigate to the IAM page and click on Policies. From there, select Create Policy.
Select Policy editor as JSON mode. Paste below inline policy and provide the policy name as IAMAccessAnalyzerGenerateFindingRecommendation.Here is the created policy details page.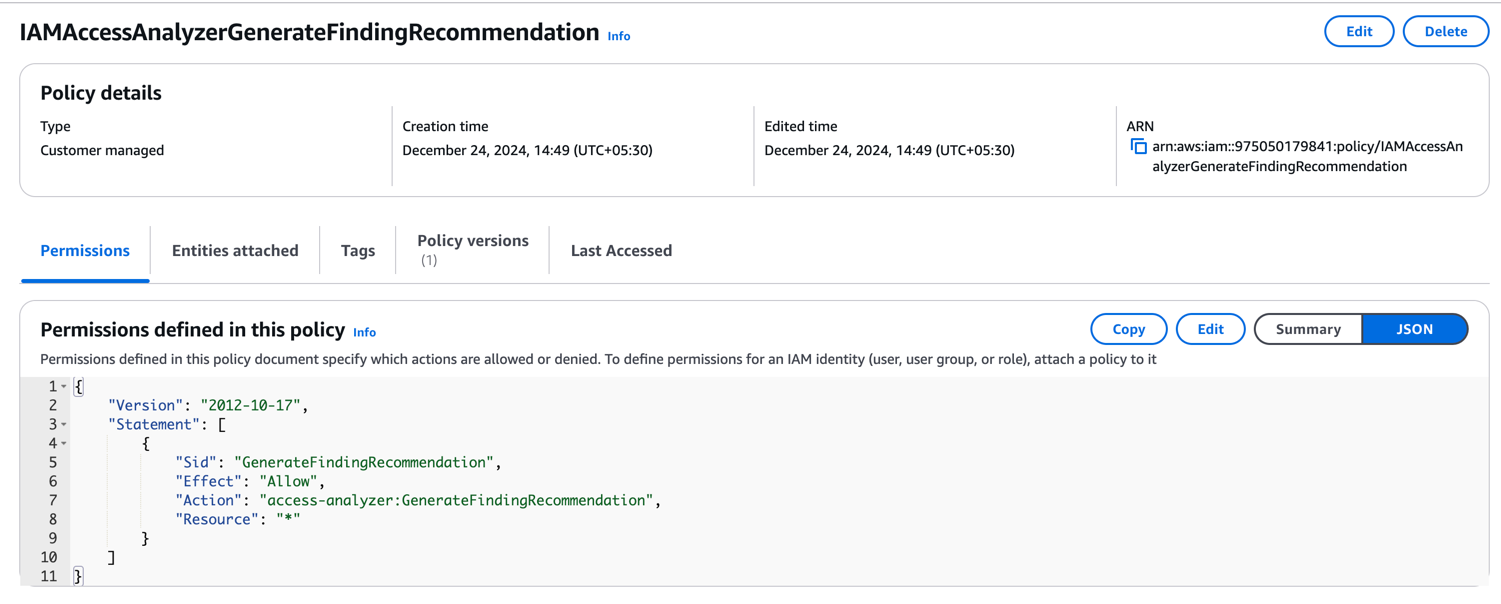

AWS Direct Access
For Leen to authenticate with AWS Access Analyzer using AWS Direct Access, we require the following:- AWS Access Key ID: A unique identifier used to authenticate requests to AWS services.
- AWS Secret Access Key: A confidential string used in conjunction with the Access Key ID to securely sign API requests to AWS services.
- AWS Region: The AWS region to pull Access Analyzer data from.
Create a new IAM User
In the AWS console, navigate to the IAM page and click on Users. From there, select Create User.We recommend that you do not check the “AWS Management Console access” option.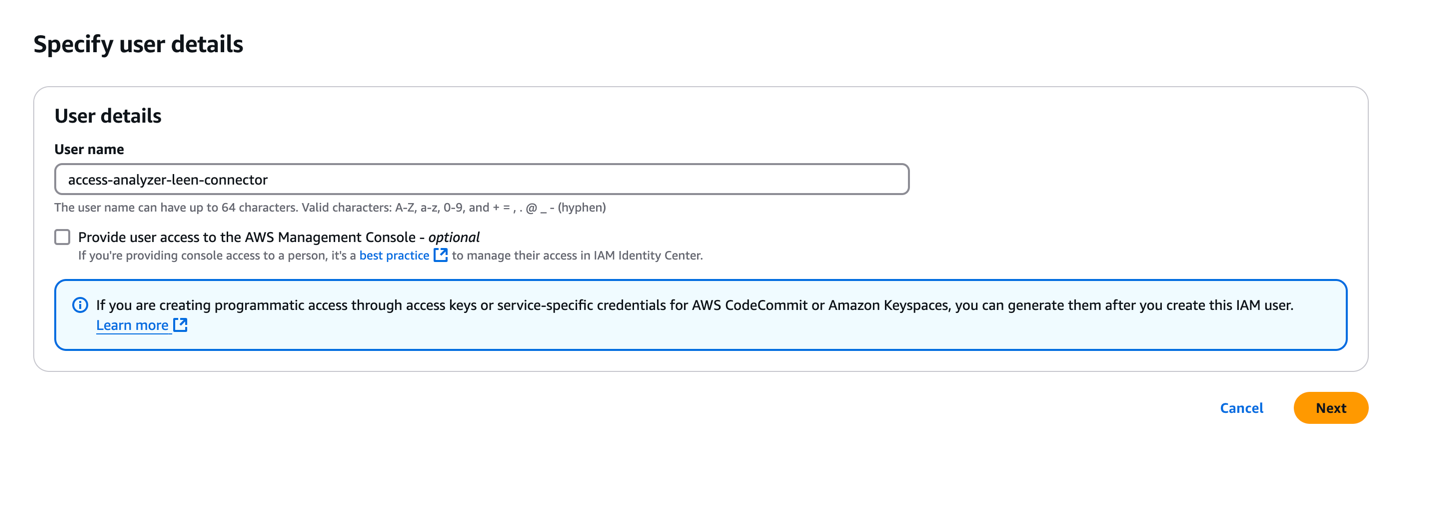

Attach Policy to User
The next step is to attach the
IAMAccessAnalyzerReadOnlyAccess and newly created IAMAccessAnalyzerGenerateFindingRecommendation policy to the user. This policy allows the user to read findings and generate recommendations from Access Analyzer.Leen Role Creation
For Leen to authenticate with AWS Access Analyzer using Leen Role Creation, we require the following:- AWS Role ARN: The Amazon Resource Name (ARN) of the IAM role that grants Leen access to your AWS Access Analyzer resources.
- External ID (Optional): A unique identifier set when creating the Leen Role.
- AWS Region: The AWS region to pull Access Analyzer data from.
Create a new IAM Role
In the AWS console, navigate to the IAM page and click on “Roles.”From there, select the “Create Role” button.For the Trusted entity type, choose the AWS Account option. Next, select Another AWS Account and enter the Leen AWS Account ID.You can optionally enable “Require External ID” and provide a unique identifier, which serves as an additional security measure to ensure that only Leen can assume the role.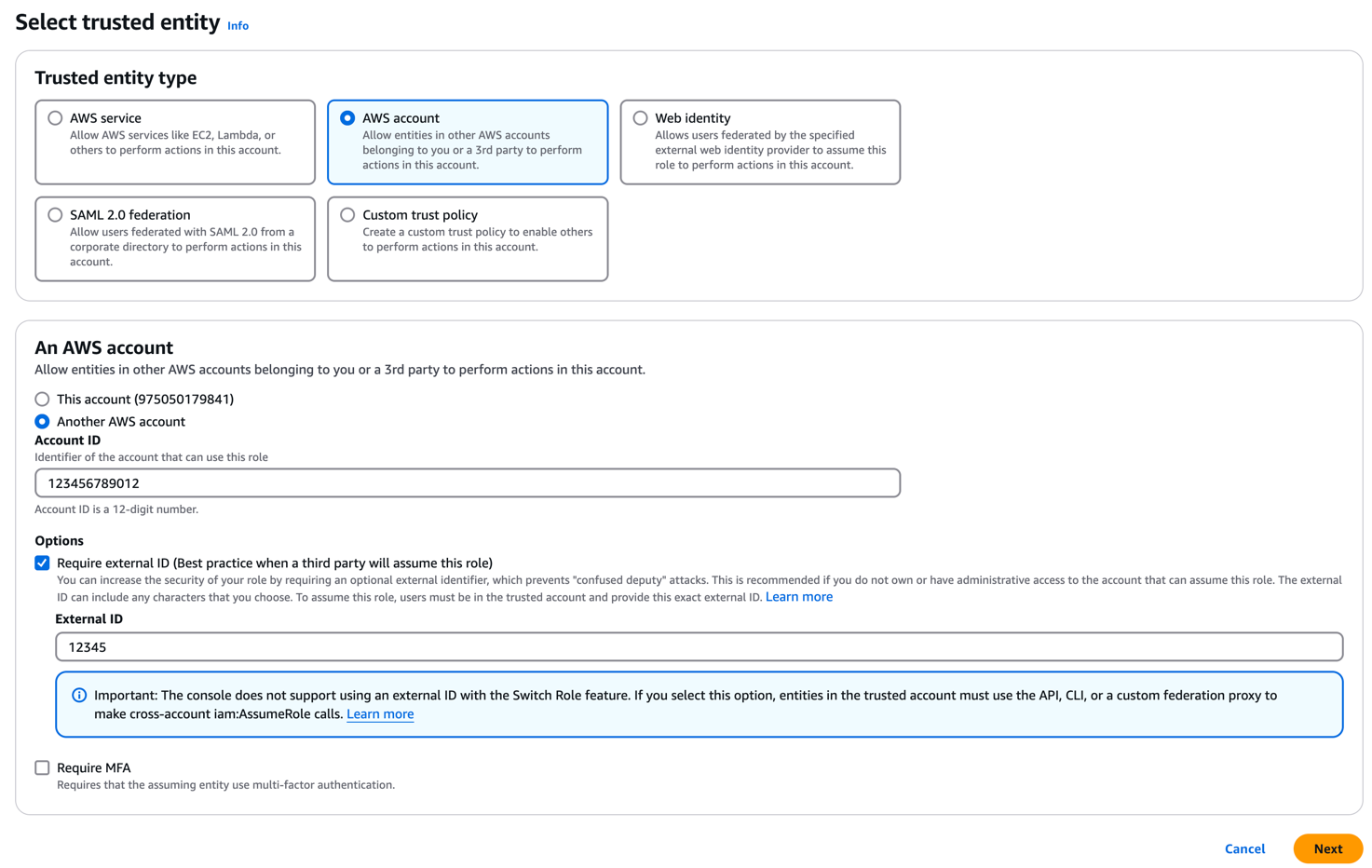
Please reach out to the Leen team to get the Leen AWS Account ID.

Add Permissions to the Role
To create the role with the minimum required permissions, we need to attach
IAMAccessAnalyzerReadOnlyAccess and newly created IAMAccessAnalyzerGenerateFindingRecommendation permissions to the role.Review and create the role
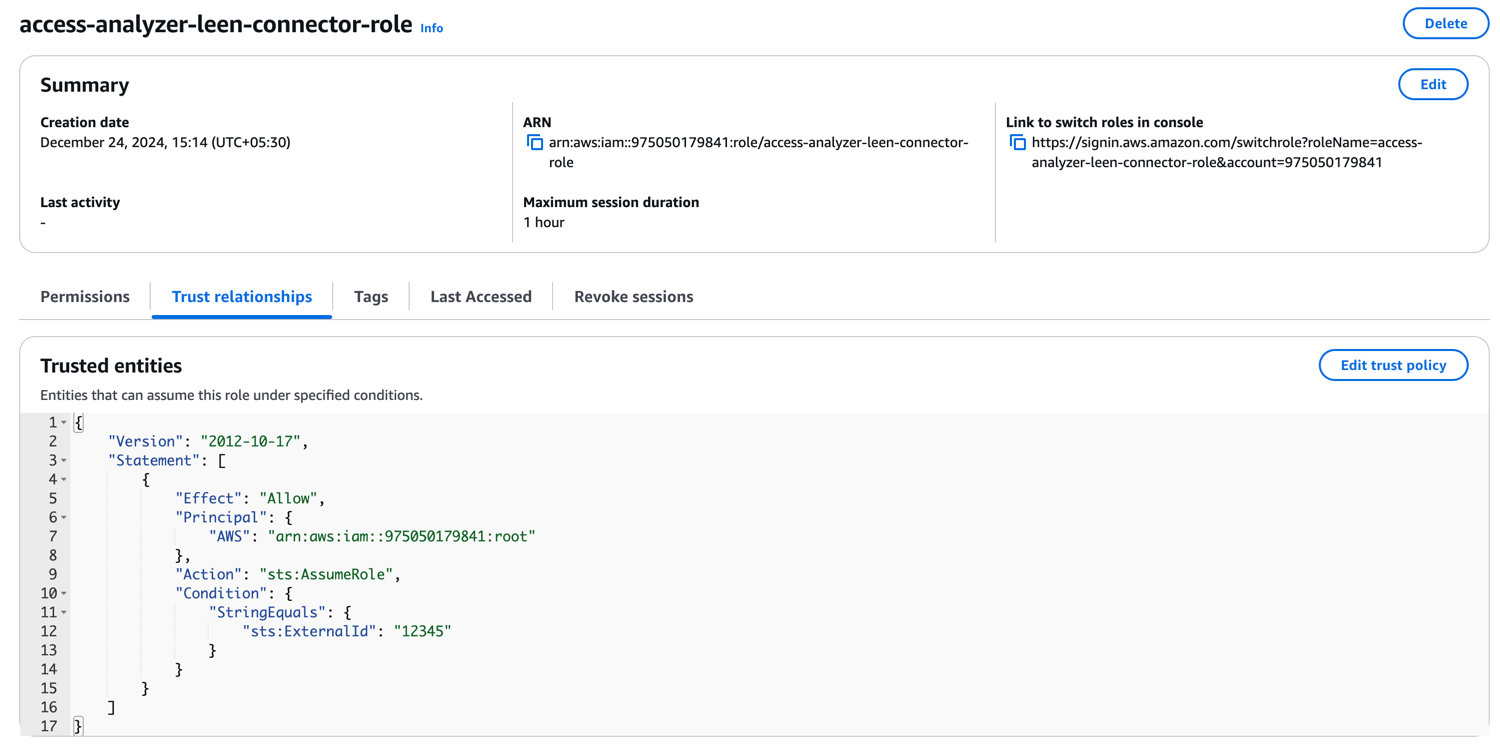
Now, give the role a name and description and review the permissions and the trust policy being created for the role.This trust policy allows the Leen AWS account to assume the role with the given access.
To create the role with the minimum required permissions, we need to attach 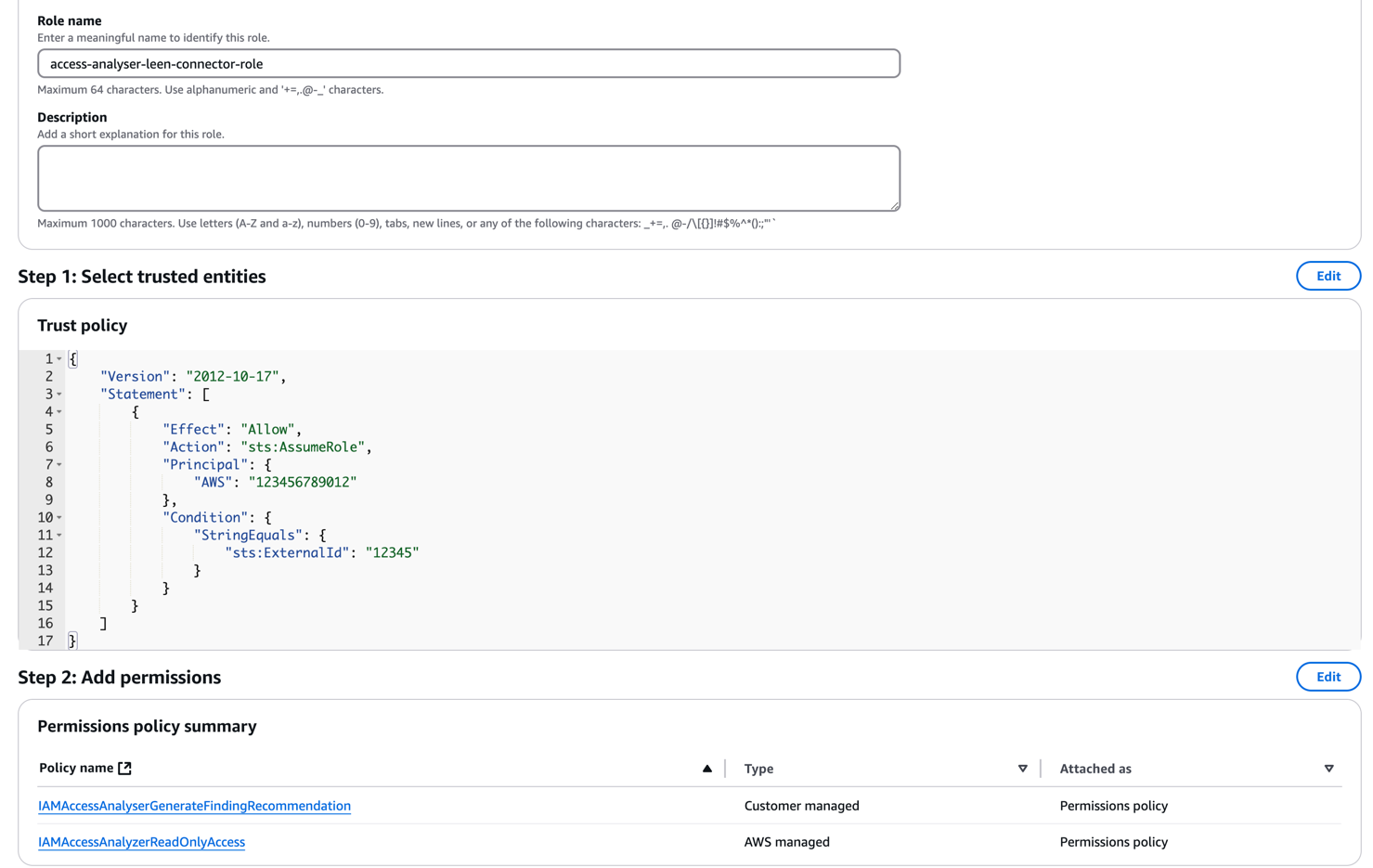
IAMAccessAnalyzerReadOnlyAccess and newly created IAMAccessAnalyzerGenerateFindingRecommendation permissions.
Role Chaining
Role Chaining is a method that allows one AWS role to assume another role, across different AWS accounts. In this setup, Leen will assume a role in your AWS account, which in turn has permissions to assume roles in your end-users’ accounts. This creates a chain of trust, granting Leen secure access to your end-user’s Access Analyzer. This method will require you to create a common role in your account with permissions to assume roles in your end-user’s account. If you already have a similar existing role setup in your AWS account that allows you to assume roles in your end-user’s account, you can update the trust relationship to allow Leen to assume that role.Leen Role Chaining requires a one time Account level setup. This is to allow Leen to setup a role and trust relationship in your account. Please reach out to the Leen team to help you setup this role.
- AWS Role ARN: The Amazon Resource Name (ARN) of the IAM role of the end-user which grants access to the common role in your account.
- External ID (Optional): Unique identifier between the end-user and the common role in your account.
- AWS Region (Optional): The AWS region to pull Access Analyzer data from.