Semgrep
Instructions on how to onboard a Semgrep Integration
Onboarding
Follow the steps below to onboard a user to our Semgrep Integration.
Create API token
Go to “Settings” -> “Tokens” -> “API Tokens” and click “Create new token”
Enable token scopes in popup
In the popup window enable following scopes
- Agent CI
- Web API
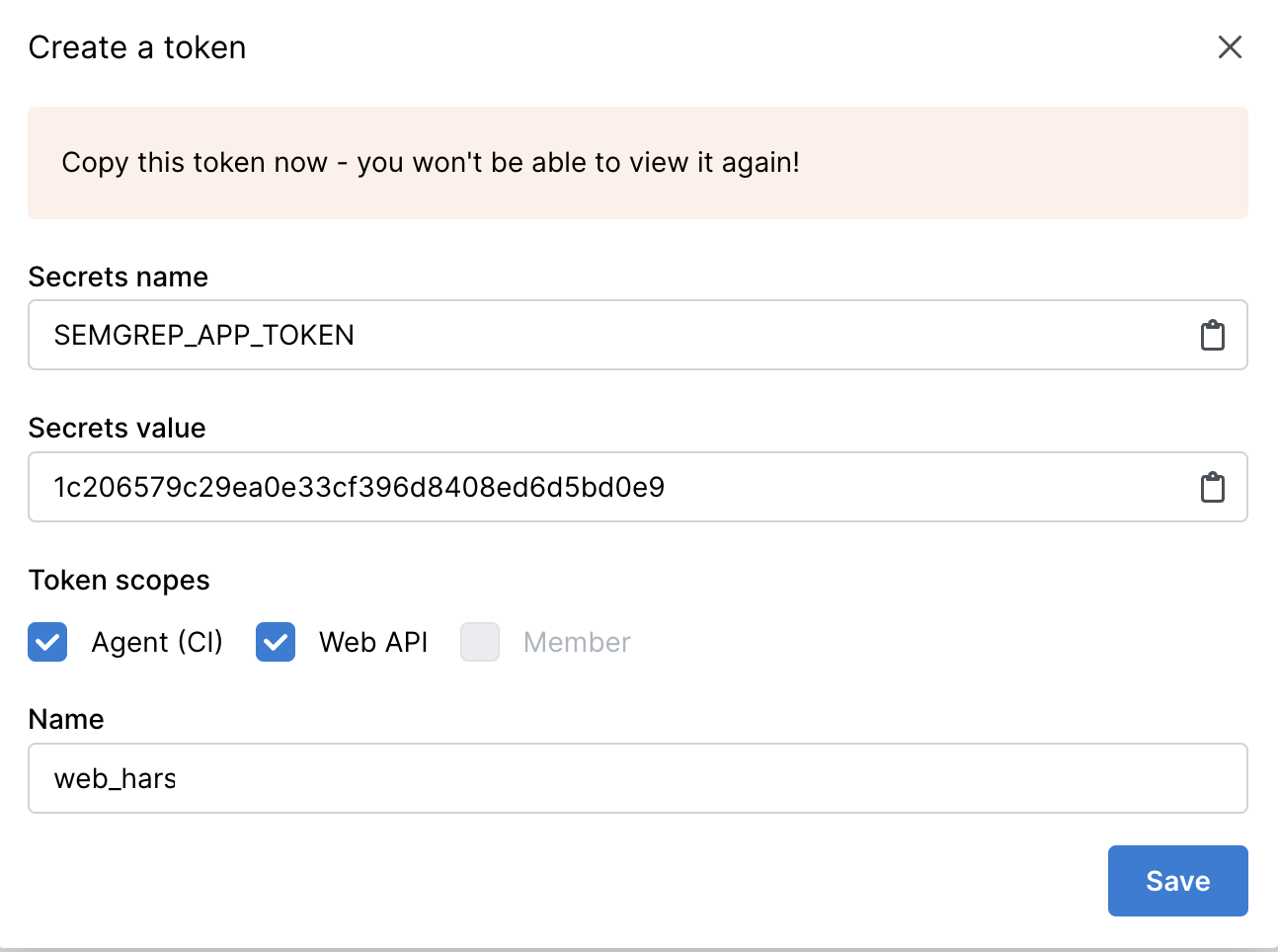
Enter Credentials
After creating the Web API token, Copy this into the Semgrep AppSec connector in its respective field.
Semgrep V1 (Issues) to V2 (Resources & Vulnerability Findings) Migration Guide – Migration Guide
Semgrep AppSec – Migration Guide
Legacy V1 Issues → V2 Vulnerability Findings & Resources
This document explains how to migrate data and code for the Semgrep connector (and, by extension, all AppSec vendors) from the legacy ScopedIssue data-model (V1) to the new ScopedVulnerabilityFindingV2 / ScopedResource models (V2).
Field-coverage & Replacement Matrix
Legend
✅ = direct or renamed field already present in V2
☑️ = moved into a nested object (e.g. vendor_attributes, resource_related, …)
🆕 = new column added to V2 schema
🚧 = still missing – add if customers rely on it
V1 ScopedIssue field | Recommended V2 location | Status |
|---|---|---|
id | id | ✅ (we reuse same UUID) |
code_repo | resource_related.affected_code.file_path or project/branch resource | ☑️ |
project_file_path | resource_related.affected_code.file_path | ☑️ |
repo_url | vendor_attributes.data.line_of_code_url (Semgrep) | ☑️ |
repo_branch_name | captured in branch‐type ScopedResource | ☑️ |
vendor | product.vendor_name | ☑️ |
vendor_id | vendor_attributes.id | ☑️ |
name | title | ✅ |
package_name | resource_related.affected_package.name | ☑️ |
package_version | resource_related.affected_package.version | ☑️ |
severity | severity | ✅ |
severity_rank (DB) | derived from severity | ✅ |
platform | resource_related.affected_platform | ☑️ |
package_manager | resource_related.affected_package.package_manager | ☑️ |
publication_time | — (redundant; use first_seen / CVE KB) | ➖ |
is_patchable | has_fix | ✅ |
type | type (CODE / DEPENDENCY / …) | ✅ |
description | description | ✅ |
vulnerability_identifiers | vendor_attributes.vulnerability_identifiers | ☑️ |
cvss_score | — (available via CVE KB) | ➖ |
state | state | ✅ |
first_seen | first_seen | ✅ |
last_seen | last_seen | ✅ |
kb_url | — (vendor & KB URLs already covered) | ➖ |
issue_url | vendor_attributes.url | ☑️ |
remediation (List[str]) | remediation (stringified) | ✅ |
vendor_data | vendor_attributes.data | ☑️ |
state_updated_at | state_updated_at | 🆕 |
connection_id | connection_id | ✅ |
unique_hash | unique_hash | ✅ |
Outstanding gaps (🚧): Currently none. All V1 data points are either mapped, intentionally dropped (➖), or available via Knowledge-Base relations.

